SAINT is is product of World Wide Digital Security (www.wwdsi.com) and is available for a fee with several supporting products or for free download (not the latest versions however).
Like all programs in the genre, it attempts to determine if a system has security flaws by examining network services, such as NFS, NIS, finger, ftp, telnet, etc. SAINT uses programs like fping and tcp_scan to find live hosts and to collect data which is then analyzed to determine the trust relationships that exist between systems and determine what vulnerabilities exist.
SAINT has web interface that makes it easy to use. The initial screen looks like this:

This is really just a menu to the various other parts of the system scanning process. Generally, you begin with Data Management with yields the following screen:
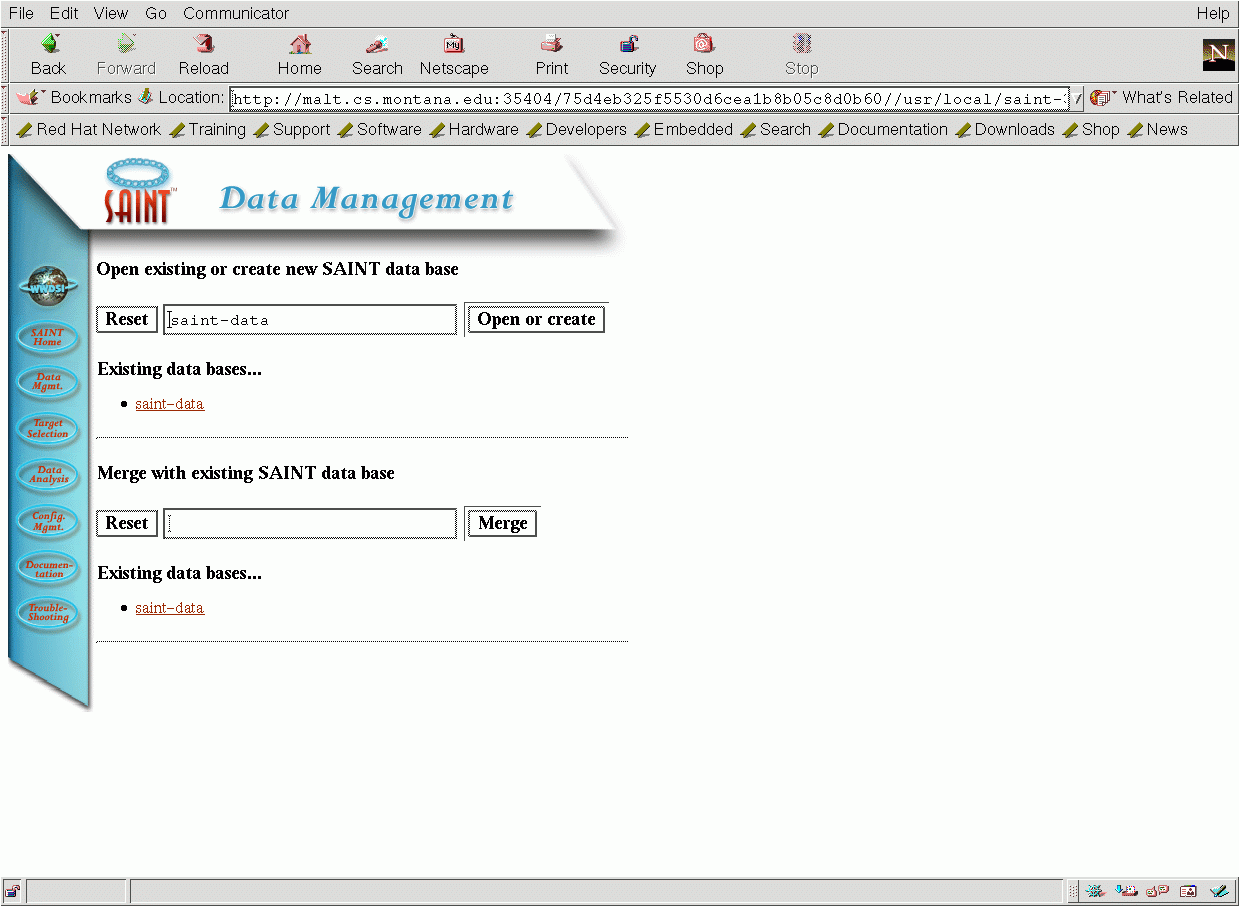
Here you type in the name of the directory where you want to store the results. This directory will be found, by default, in the Saint home directory (typically /usr/local/saint-X.Y.Z/results. You can also merge the new data with an existing database.
In the directory you will find a list of files such as this:
all-hosts cve facts todo a list of files such as this:
These files contain the data collected, but you can use Saint to present them.
Next you select the target or targets that you want to scan. This can either be a list typed in, as shown below, or a list maintained in a file, such as you would use to do regular scans.
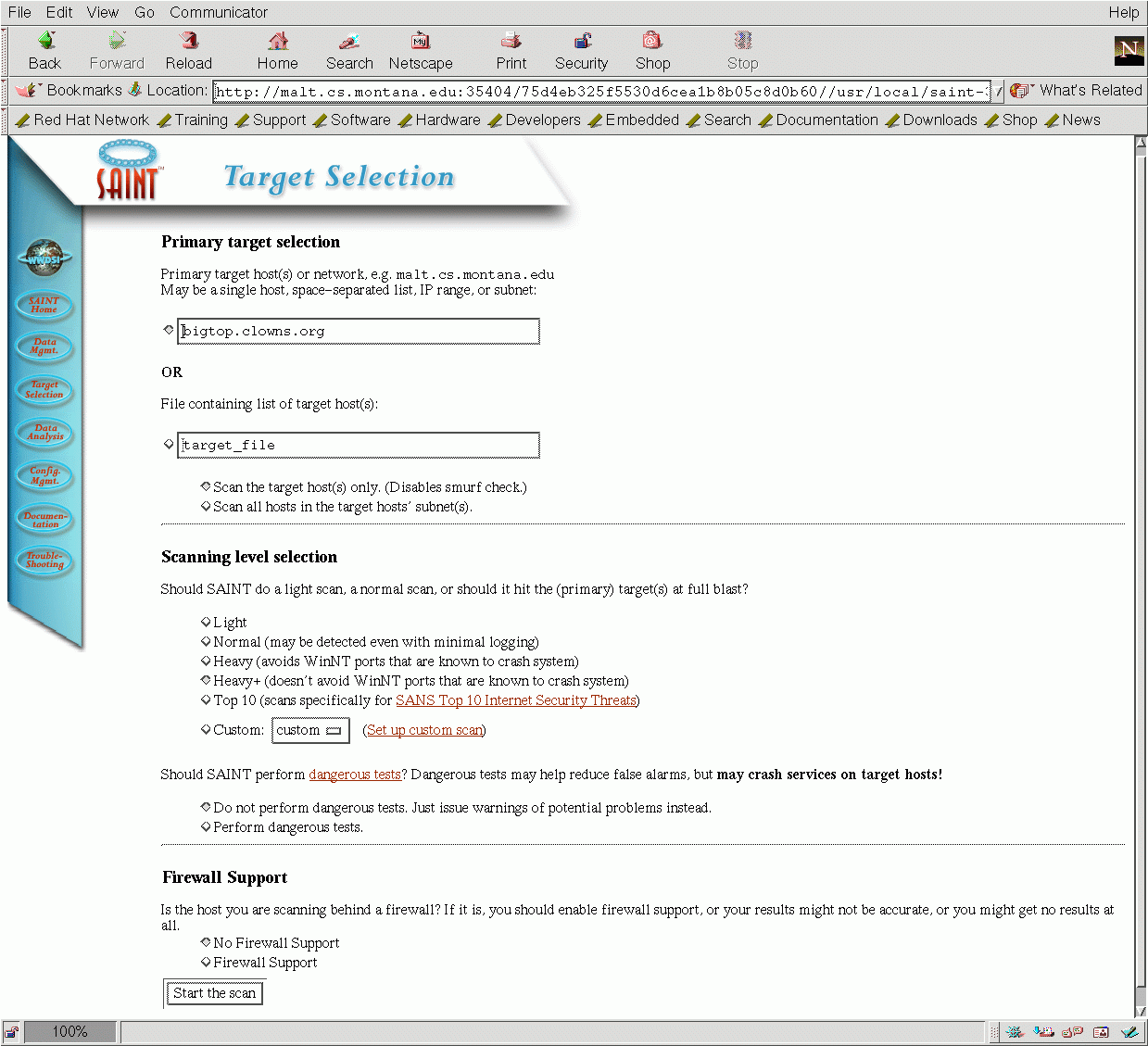
You specify the type of scan that you want, from minimal (Light) to Heavy, and you can customize the scan or choose from the SANS top 10. If the host you are scanning has firewall protection, you need to indicate that so that Saint can adjust.
When you are ready, press Start the Scan and wait for the results. While the scan takes place, you will see output telling you what operations are being performed.

The results from this version are somewhat limited, primarily because they want to sell you the products that will provide more information. It shows a page like this:
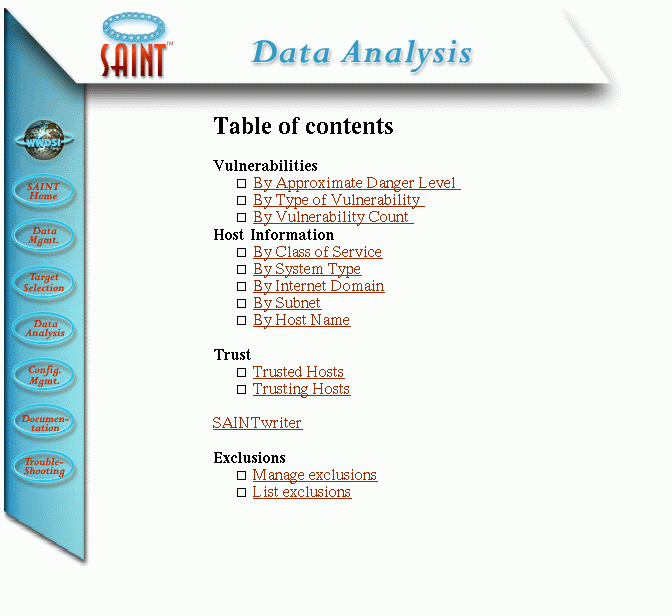
which provides different views of the data. For example, the Host By Class of Services shows this:
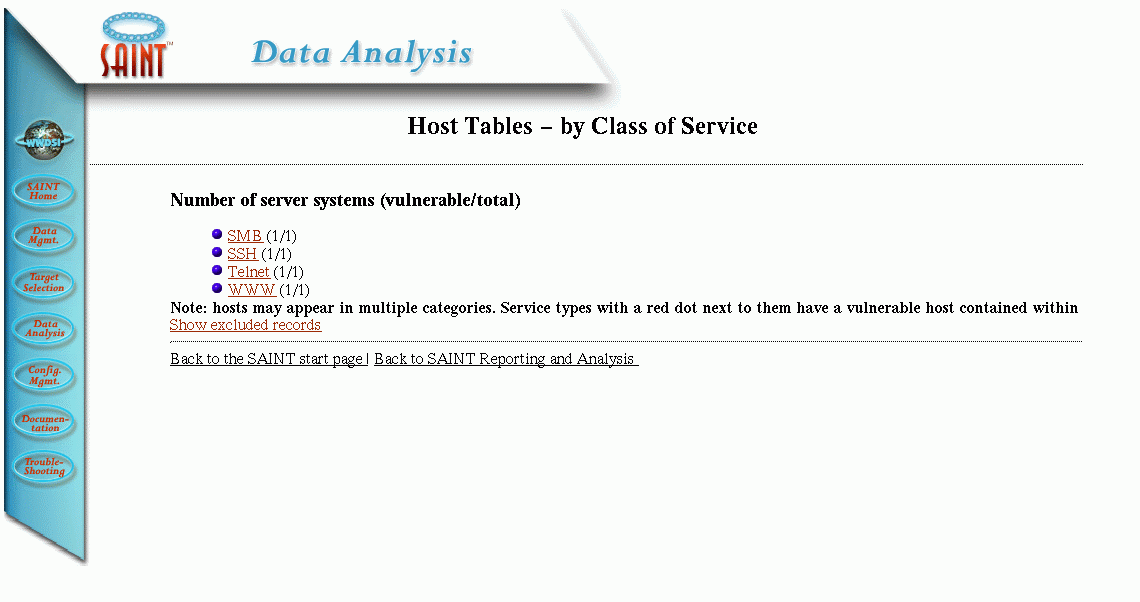
The given host has four vulnerabilities, SMB, SSH, Telnet and WWW, each with one problem.
The Danger Levels view shows the problems ranked by the potential danger of the vulnerability.
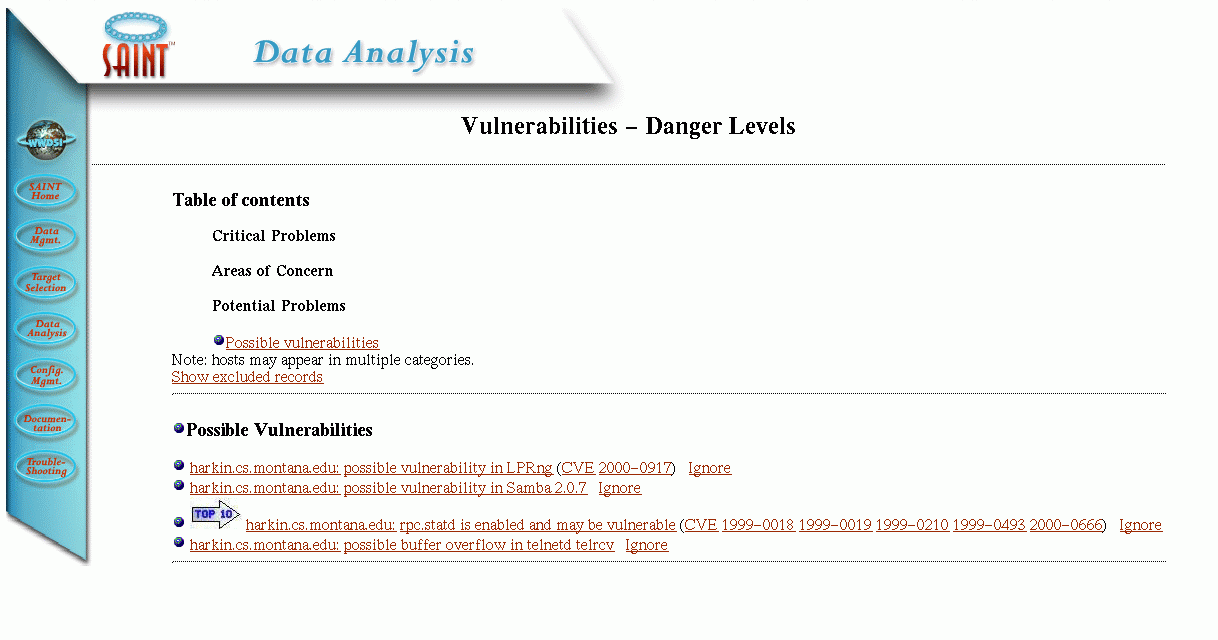
If you click on one of these, it will show a report like this:
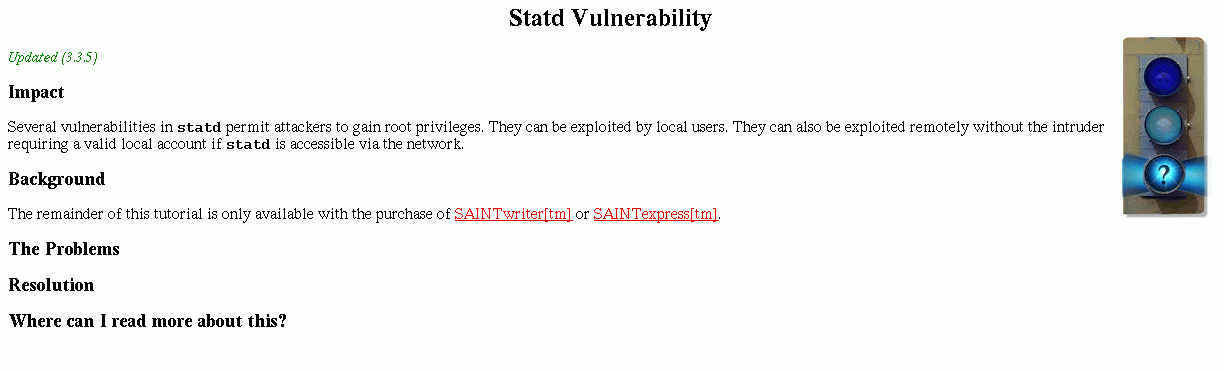
Unfortunately, it shows only a partial report in the free version.
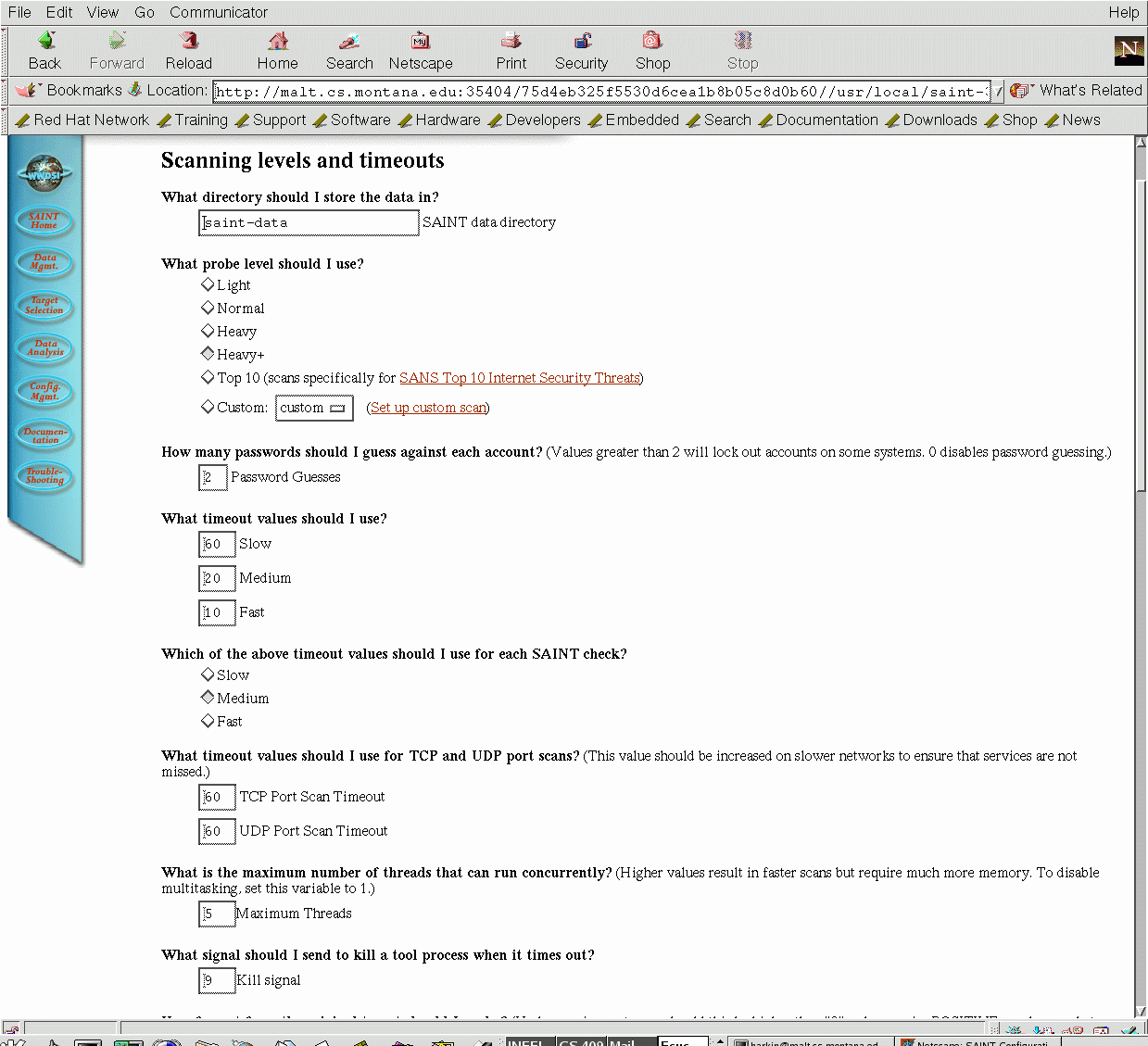
Finally, the configuration page allows you to configure the activities of Saint, including tests to run, timeout values and so on.