

Masquerading, where a system acts on behalf of other systems, such as when an ISP server accesses network services on behalf of a dialup user.
Multiple Servers, where there is more than one system that can provide a service, and you want to decide which to choose based on which of them is functional, or to balance loads between them.
Proxying, where the real destination of a packet is changed for another. For example, sending all email or http traffic to a special server that is isolated to improve security.
The possible uses of NAT are relatively unlimited as you will see.
So the simplest explanation of NAT is that to achieve some goal, the source and/or destination address is modified prior to forwarding a packet.
If you are familiar with netfilter, you have seen a diagram like this:
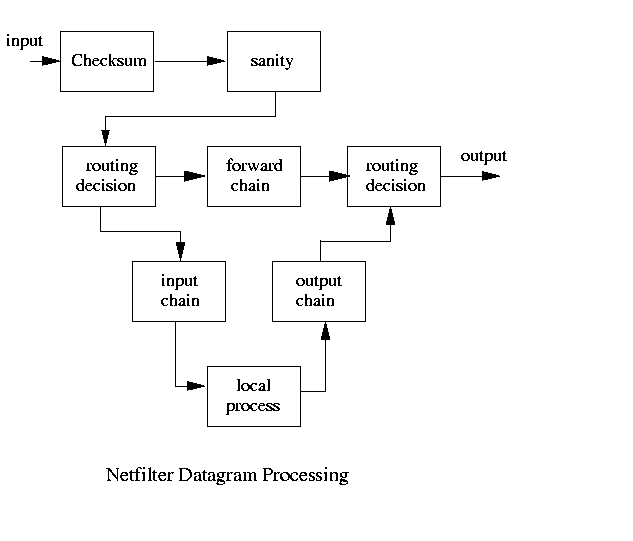
iptables has three tables, filter, nat and mangle. Each table has a predefined set of chains that relate to a particular part of the packet transmission process. Normally, you use the filter table and the INPUT and OUTPUT chains chains to filter traffic. The FORWARD chain of filter is used to perform routing chores.
What we are interested are the nat table and its builtin chains PREROUTING, OUTPUT and POSTROUTING; and the mangle table and its builtin chains, PREROUTING and OUTPUT.
For the nat table, the PREROUTING chain is for altering packets before they are routed and POSTROUTING is for altering packets as they are leaving the system. The OUTPUT chain is for altering packets that are generated locally before they are routed.
For the mangle table, the definition is the same for PREROUTING and OUTPUT. More recent kernels also support the mangle table chains INPUT, FORWARD and POSTROUTING. In other words, you can mangle a packet at just about any point in the process.
There are two types of NAT, source NAT and destination NAT. Source NAT changes the source address of a packet before it is sent, so that it appears to come from a system other than the actual sender. This is masquerading, and takes place at postrouting, right before the packet is moved to the output chain.
Destination NAT changes the destination of a packet and it takes place at prerouting, before the actual routing is done. This allows the new destination to be used to decide if the packet should be routed to the local system, or to the forward chain. This is used for transparent proxying, port forwarding and application such as load balancing.
| iptables -t nat -A POSTROUTING -o eth0 -j SNAT --to-source 192.168.1.7 |
This rules specifies the a new rule is to be appended to the POSTROUTING chain of the nat table; the rule applies to the eth0 interface and the target is SNAT (Source NAT) and the source address will be changed to 192.168.1.7.
Suppose you are sending a packet from 192.168.1.104, but you don't want that address known to the outside world. The receiver of the message will think that the IP address of the sender is 192.168.1.104, and will send any response to that address. That means that you also have to plan to get the response back to the right place, which can be done by having your host respond as though it has two (or more) ip addresses with this command:
| ip address add 192.168.1.7 dev eth0 |
which will cause 192.168.1.104 to also respond to any ARP request for 192.168.1.7 as well.
That's pretty neat, but what else can you do. Suppose you have a room full of systems (call it a lab) that you don't want to expose to the outside world. This might be a security problem, a lack of IP addresses or just a desire to limit what the people using these systems can do. You would set up a system (call it the gateway) with two interface cards, one connected to the outside world (eth0) and one connected to your lab (eth0). On the side connected to the outside world you have a normal IP address such as 155.155.155.155, and on the other side you have a bogus address, such as 192.168.1.1. The systems in the lab all have addresses of the form 192.168.1.N and will all list your gateway as their default gateway, so that messages headed for the outside world will go through the gateway.
As messages are received from the lab systems, they can be filtered, but they also must be masqueraded since their IP addresses are not truly legal. So you might have rules like this:
| iptables -t nat -A FORWARD -i eth1 |
| iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE |
The first rule forwards all traffic from eth1 and the second sends it out over eth0 with the address of the host (e.g. 155.155.155.155). The MASQUERADE target causes the source address to be changed to the address of the outgoing interface.
Another possible first rule is:
| iptables -t nat -A FORWARD -s 192.168.1.0/24 |
You might want to be more explicit in the case where the gateway has other functions:
| iptables -t nat -A FORWARD -i eth1 -d !155.155.155.155 |
| iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE |
So packets destined for the gateway are not forwarded, but packets destined for other hosts are:
If you were using a modem to connect to the outside world but had a SOHO (Small Office Home Office) network going, you might have a PPP interface rather than an ethernet interface on the outgoing side. Simply change -o eth0 to -o ppp0 (at least that's the likely scenario) in the commands.
One other thing that you can do with SNAT is modify source addresses to a range. This can be important if you are handling a large number of hosts, such as acting as a gateway for a network. In order to perform its functions, netfilter has to remember what packets it has sent which can lead to problems. For example, if two backnet hosts open a connection to the same host with the same port (e.g. they both connect to a host with port 555), and both are SNAT'ed to the same address, it will be impossible to tell them apart. To alleviate such problems, you can map to a range of addresses like this:
| iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -j SNAT --to-source 10.0.0.100-10.0.0.200 |
and you can also map ports as necessary (for tcp or udp), although netfilter will do some of this on its own.
| iptables -t nat -A POSTROUTING -p tcp -s 192.168.1.0/24 --sport 512-1023 |
| -j SNAT --to 10.0.0.100:1024-10000 |
| iptables -t nat -A POSTROUTING -p tcp -s 192.168.1.0/24 --sport 512-1023 |
| -j MASQUERADE --toports 1024-10000 |
Simple DNAT
In the simplest case, all you might want to do is take and incoming packet and send it somewhere else:
| iptables -t nat -A PREROUTING -i eth0 -j DNAT --to-destination 192.168.1.1 | ||
| iptables -t nat -A PREROUTING -p tcp --dport sendmail -j DNAT | ||
| --to-destination 192.168.1.1 | ||
| iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT | ||
| --to-destination 192.168.1 --to-port:8080 |
The first sends any packet coming in on eth0 to 192.168.1.1. The second sends all sendmail traffic to a different host, and the third sends all web traffic to another host (a web server) where the web server runs at a different port (probably for protection purposes).
If you want to redirect traffic on the same host, there is a special DNAT known as redirection:
| iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-port 8080 |
Load Balancing
Another use of DNAT is to implement a load balancing solution for a service like a web server. Suppose you have three web servers, 192.168.1.1 through 192.168.1.3. You could balance the requests to these three servers with:
| iptables -t nat -A PREROUTING -p tcp --dport httpd -j DNAT |
| --to-destination 192.168.1.1-192.168.1.3 |
Packets will be distributed uniformly between the three servers. Note that this does not take the actual load into account, only the perceived load based on packet count. If you wanted something more robust, you could implement a load balancing server and direct all the traffic there.
System Protection
You can also use DNAT to protect your system from certain types of misbehavior. For example, packets with an address of 192.168.0.0/16, 10.0.0.0/8, or 172.16.0.0/12 are bad packets:
| iptables -t nat -A PREROUTING -i eth0 -s 192.168.0.0/16 -j DROP | ||
| iptables -t nat -A PREROUTING -i eth0 -s 172.16.0.0/12 -j DROP | ||
| iptables -t nat -A PREROUTING -i eth0 -s 10.0.0.0/8 -j DROP |
and you might want to dump certain types of TCP packets that are often used to attack a system. Primarily SYN, ACK or RST packets that are out of place:
| iptables -t nat -A PREROUTING -p tcp !-syn -m state --state NEW -j LOG | ||
| --log-prefix "Improper sync state" | ||
| iptables -t nat -A PREROUTING -p tcp !-syn -m state --state NEW -j DROP |
MARK refers to specialized routing functions and TTL refers to changing the time to live field on a packet. The only reason you might change the time to live would be to insure that a packet doesn't get forwarded beyond some particular point.
TOS refers to the Type of Service field in the IP packet and has the following values:
| Value | Meaning | |
|---|---|---|
| 16 | Minimize delay | |
| 8 | Maximize throughput | |
| 4 | Maxmize reliability | |
| 2 | Minimize cost | |
| 0 | Normal service |
This might typically be used to set the type of service for packets going to particular services. For example:
| iptables -t mangle -A OUTPUT -p tcp --dport telnet -j TOS --set-tos 8 | ||
| iptables -t mangle -A OUTPUT -p tcp --dport smtp -j TOS --set-tos 16 | ||
| iptables -t mangle -A PREROUTING -p tcp --dport telnet -j TOS --set-tos 8 | ||
| iptables -t mangle -A PREROUTING -p tcp --dport http -j TOS --set-tos 8 |
A common element of network security architectures these days is a DMZ which comes from the term demilitarized zone - a place where no one is armed and yet, no one is trusted. The idea is that your network uses one of the locally reserved IP address spaces so that it is virtally unpenetrable and the IP address translations as well as all the necessary firewalling is done by the DMZ system. The challenge here is to create the iptable rules for the DMZ and for the internal handling of traffic to the DMZ. Here is an example of DMZ rules